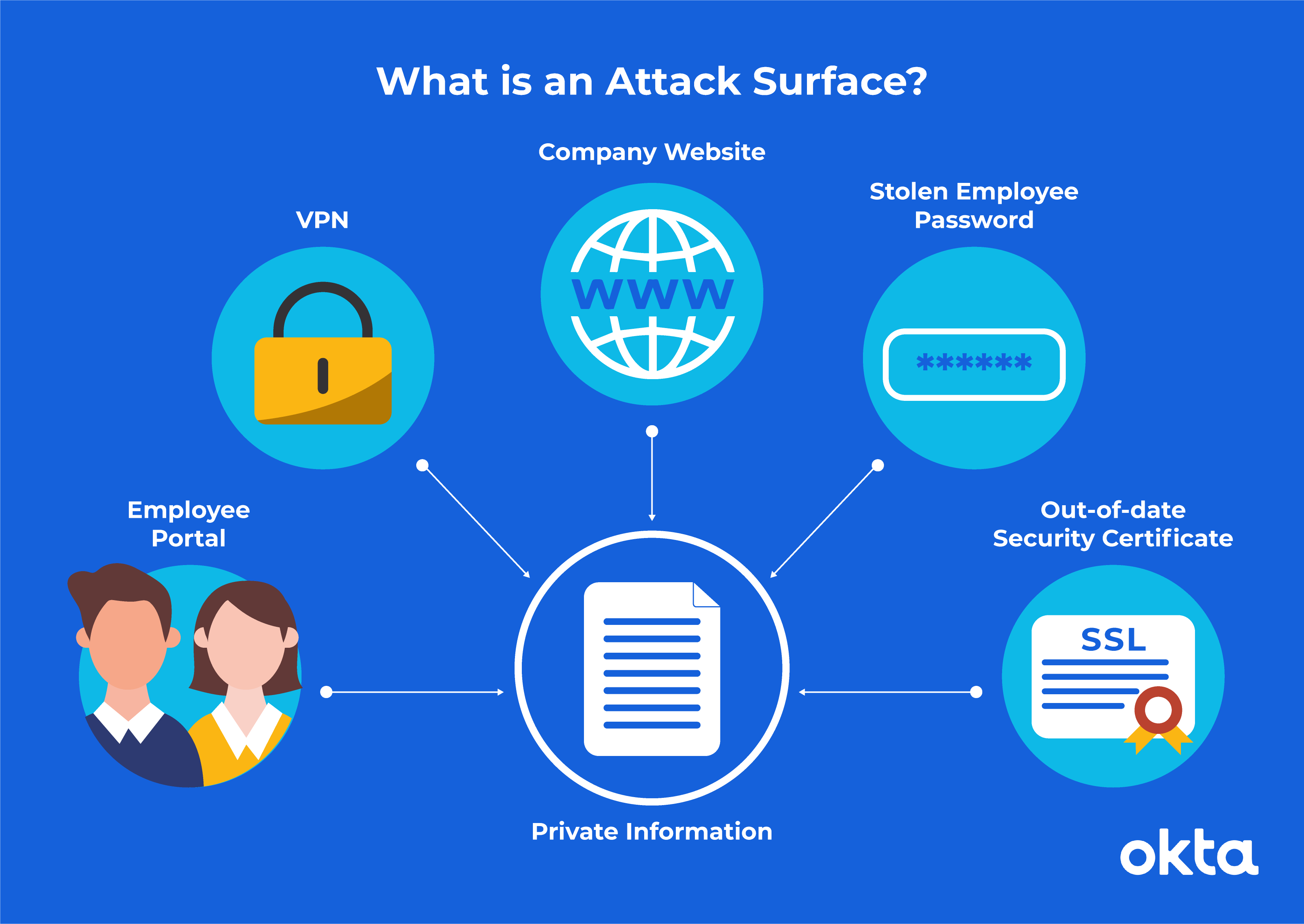
Explore Randori Recon What is an attack surface An organizations attack surface is the sum of vulnerabilities pathways. The attack surface is the number of all possible points or attack vectors where an unauthorized user can access a. An attack surface is a cybersecurity term that describes all the possible points that an attacker could. An attack surface is essentially the overall vulnerability that is created by a business digital network over which it..
Explore Randori Recon What is an attack surface An organizations attack surface is the sum of vulnerabilities pathways. The attack surface is the number of all possible points or attack vectors where an unauthorized user can access a. An attack surface is a cybersecurity term that describes all the possible points that an attacker could. An attack surface is essentially the overall vulnerability that is created by a business digital network over which it..
. The attack surface is the number of all possible points or attack vectors where an unauthorized user can access a. Explore Randori Recon What is an attack surface An organizations attack surface is the sum of vulnerabilities pathways. An attack surface is essentially the overall vulnerability that is created by a business digital network over which it. The Attack Surface of an application is The sum of all paths for datacommands into and out of the application and the. Attack surface management ASM is the continuous discovery analysis remediation and monitoring of the. ..
An organizations attack surface is the sum of vulnerabilities pathways or methodssometimes called attack. The attack surface is the number of all possible points or attack vectors where an unauthorized user can access a. An attack surface is essentially the overall vulnerability that is created by a. An attack surface is a cybersecurity term that describes all the possible points that an attacker could. The attack surface of a software environment is the sum of the different points for attack vectors. An attack surface is the sum of all possible security risk exposures in an organizations..

Comments